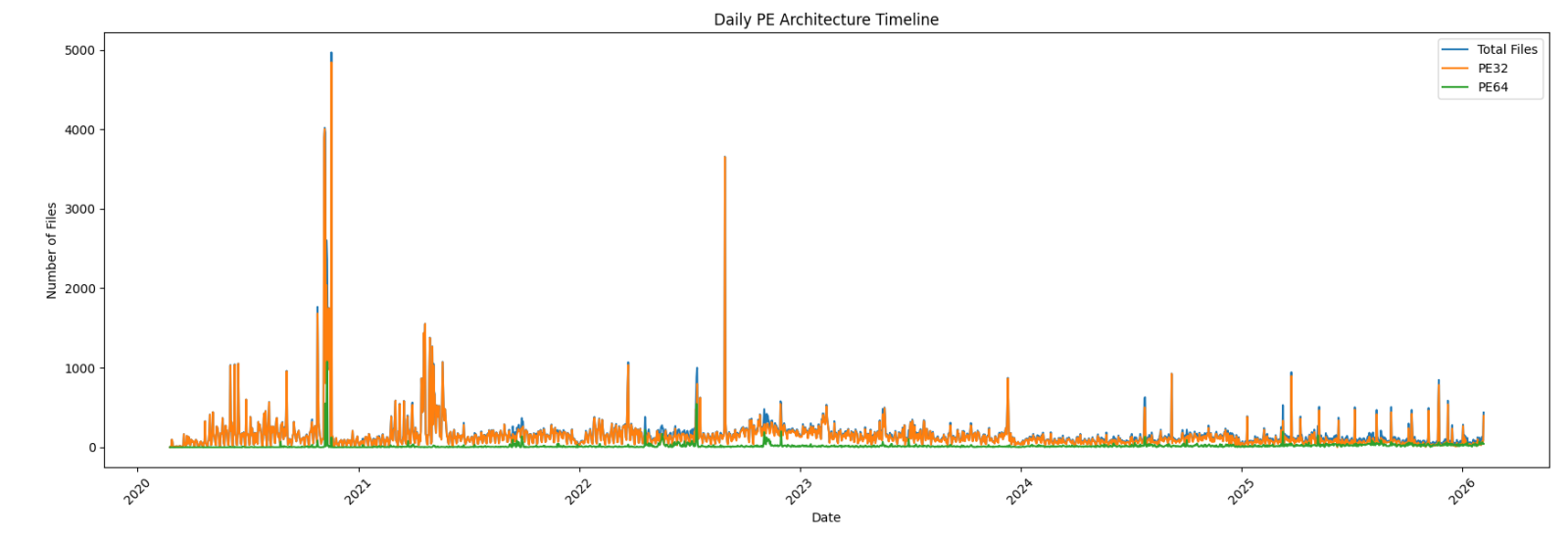
In 2022 (time flies!), I wrote a diary about the 32-bits VS. 64-bits malware landscape[1]. It demonstrated that, despite the growing number of 64-bits computers, the “old-architecture” remained the standard. In the SANS malware reversing training (FOR610[2]), we quickly cover the main differences between the two architectures. One of the conclusions is that 32-bits code is still popular because it acts like a comme denominator and allows threat actors to target more Windows computers. Yes, Microsoft Windows can smoothly execute 32-bits code on 64-bits computers. It is still the case in 2026? Did the situation evolved?
Last week, I make the exact same exercise and generated some statistics. I download the malware archive from Malware Bazaar[3] and re-executed my YARA rule.
Some basic numbers:
- 2.167 ZIP archives (one per day)
- 1.120.034.288.112 bytes (1.1TB)
- Time line covered: from 2020/02/24 – 2026/02/05
- 346.985 samples analyzed (only PE files)
- 312.307 32-bits samples
- 34.677 64-bits samples
- 11% of 64-bits samples
First, an overview of the global malware trend over the complete time period:
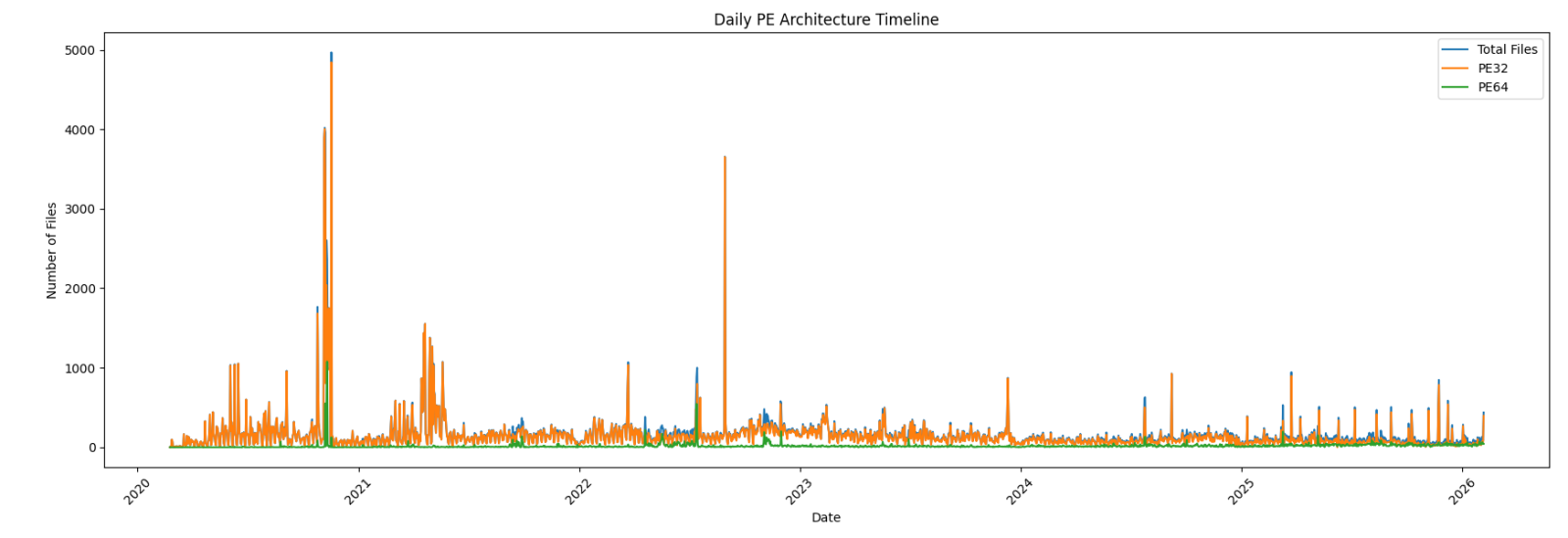
Zoom on the last year:
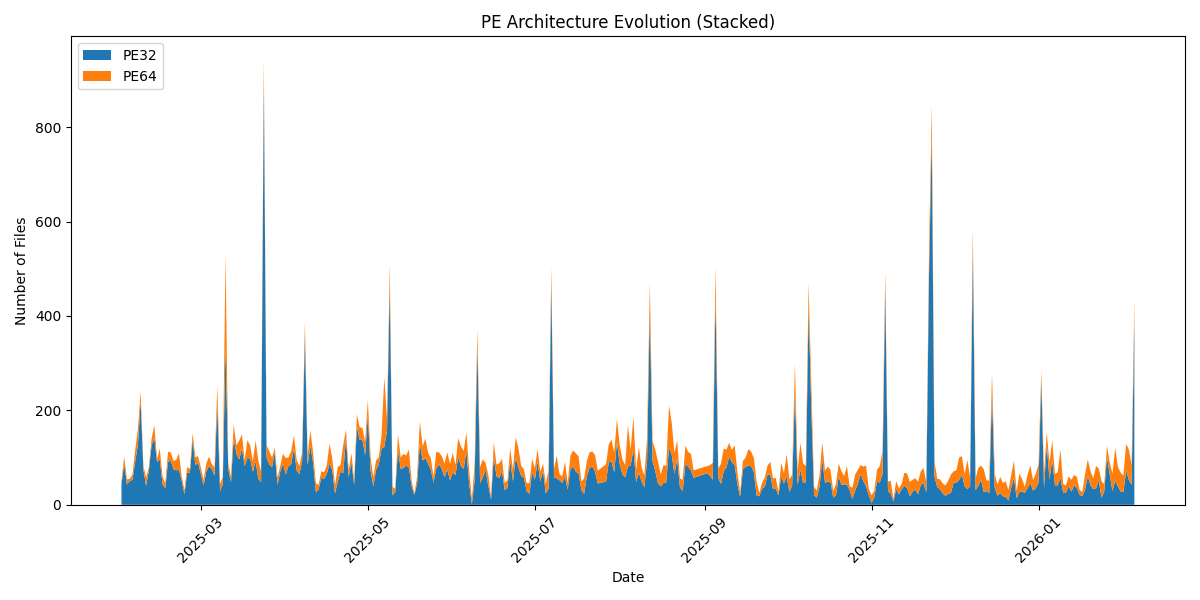
Now the interesting graph: the 64-bits sample trend over the complete period:
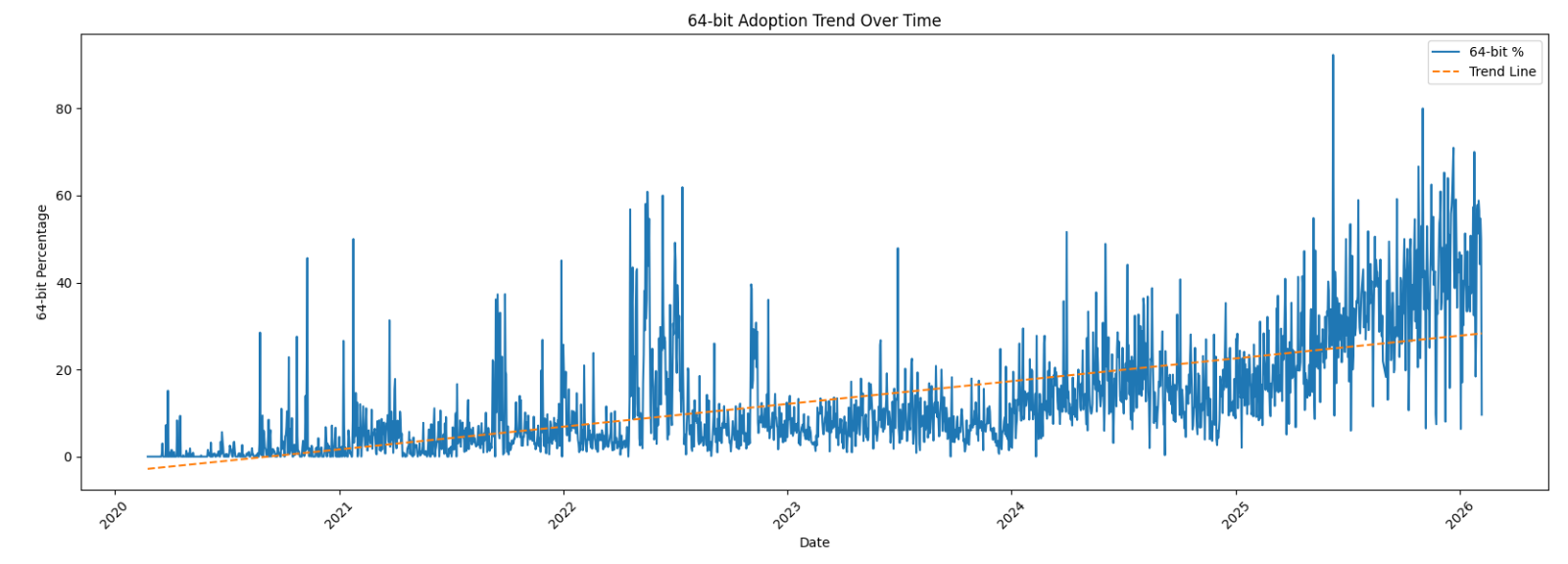
Zoom on the last year:
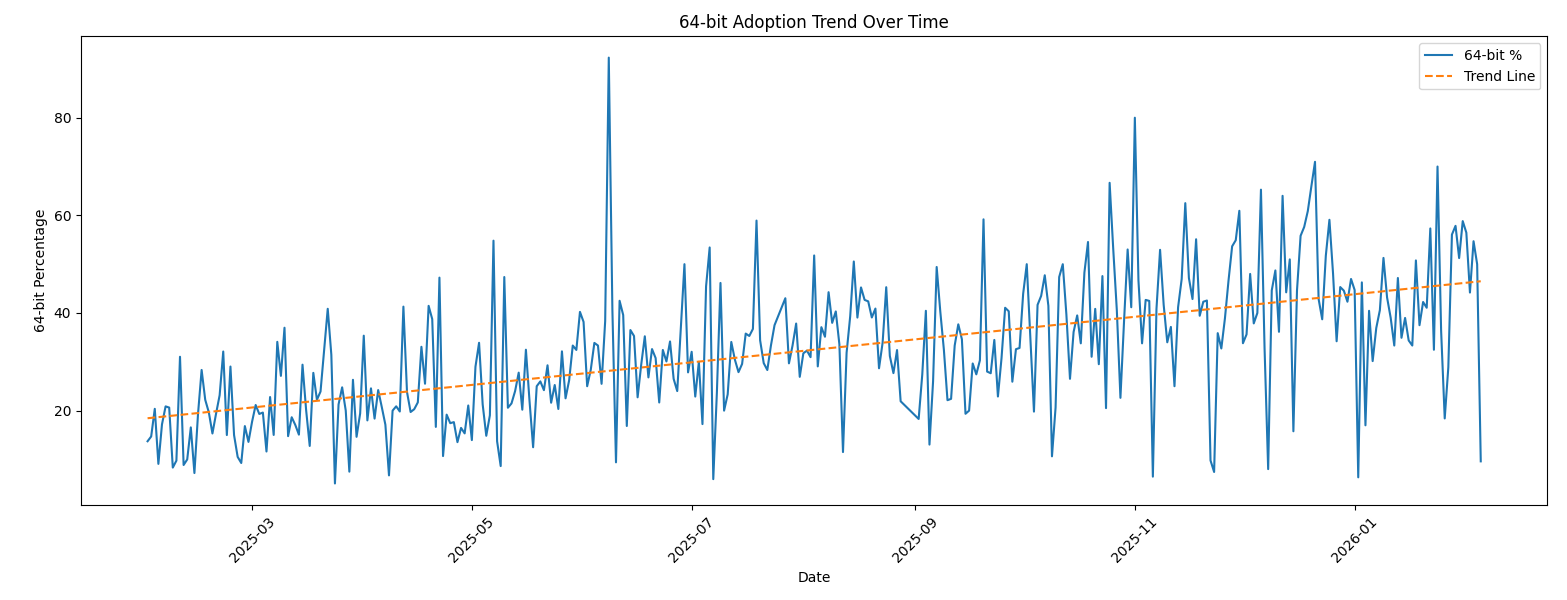
We can clearly see that, compared to 2022, there is now a trend in 64-bits code! Have a look at the last 30 days:
| Date | Total Files | 32-bits | 64-bits |
| 2026-01-07 | 65 | 41 | 24 |
| 2026-01-08 | 69 | 41 | 28 |
| 2026-01-09 | 117 | 57 | 60 |
| 2026-01-10 | 44 | 25 | 19 |
| 2026-01-11 | 41 | 25 | 16 |
| 2026-01-12 | 60 | 40 | 20 |
| 2026-01-13 | 53 | 28 | 25 |
| 2026-01-14 | 63 | 41 | 22 |
| 2026-01-15 | 59 | 36 | 23 |
| 2026-01-16 | 32 | 21 | 11 |
| 2026-01-17 | 27 | 18 | 9 |
| 2026-01-18 | 65 | 33 | 32 |
| 2026-01-19 | 96 | 60 | 36 |
| 2026-01-20 | 71 | 41 | 30 |
| 2026-01-21 | 56 | 33 | 23 |
| 2026-01-22 | 82 | 35 | 47 |
| 2026-01-23 | 77 | 52 | 25 |
| 2026-01-24 | 50 | 15 | 35 |
| 2026-01-25 | 44 | 28 | 16 |
| 2026-01-26 | 125 | 102 | 23 |
| 2026-01-27 | 90 | 64 | 26 |
| 2026-01-28 | 66 | 29 | 37 |
| 2026-01-29 | 121 | 51 | 70 |
| 2026-01-30 | 80 | 39 | 41 |
| 2026-01-31 | 68 | 28 | 40 |
| 2026-02-01 | 62 | 27 | 35 |
| 2026-02-02 | 129 | 72 | 57 |
| 2026-02-03 | 117 | 53 | 64 |
| 2026-02-04 | 84 | 42 | 42 |
| 2026-02-05 | 437 | 395 | 42 |
We are getting close to a 50-50 repartition!
???????
[1] https://isc.sans.edu/diary/32+or+64+bits+Malware/28968
[2] https://www.sans.org/cyber-security-courses/reverse-engineering-malware-malware-analysis-tools-techniques
[3] https://bazaar.abuse.ch
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key